37++ Which of the following is the most widely used wireless network encryption for home wireless networks information
Home » Background » 37++ Which of the following is the most widely used wireless network encryption for home wireless networks informationYour Which of the following is the most widely used wireless network encryption for home wireless networks images are available in this site. Which of the following is the most widely used wireless network encryption for home wireless networks are a topic that is being searched for and liked by netizens today. You can Download the Which of the following is the most widely used wireless network encryption for home wireless networks files here. Download all free photos and vectors.
If you’re searching for which of the following is the most widely used wireless network encryption for home wireless networks images information related to the which of the following is the most widely used wireless network encryption for home wireless networks topic, you have pay a visit to the right blog. Our site always gives you suggestions for viewing the highest quality video and picture content, please kindly hunt and locate more informative video articles and graphics that fit your interests.
Which Of The Following Is The Most Widely Used Wireless Network Encryption For Home Wireless Networks. It was developed to protect the wireless data between Clients and Access Points APs towards hackers. Today WPA2 is probably the most commonly used method to. WebTitan Cloud for WiFi requires no hardware purchases or software downloads as it is 100 cloud-based can be managed and monitored from any location and can help protect you against the most common wireless network attacks. WEP WPA and WPA2.
 Understanding Wireless Networks A Simple Guide For Business Businesstechweekly Com From businesstechweekly.com
Understanding Wireless Networks A Simple Guide For Business Businesstechweekly Com From businesstechweekly.com
Laura a customer has instructed you to configure her home office wireless access pointShe plans to use the wireless network for finances and has requested that the network be setup with the highest encryption possible Additionally Laura knows that her neighbors have wireless networks and wants to ensure that her network is not being interfered with by the other networks. Understanding encryption on how it works will help you decide which protocol will protect your data. AES The Advanced Encryption Standard AES encryption algorithm a widely supported encryption type for all wireless networks that contain any confidential data. The 900 MHz band is the most commonly used. In a wireless network we have Access Points which are extensions of wireless ranges that behave as logical switches. However these frequencies are often used by other wireless home devices such as cordless headphones or garage door openers and therefore they are subject to interference.
Wireless Network Technology Difficulty.
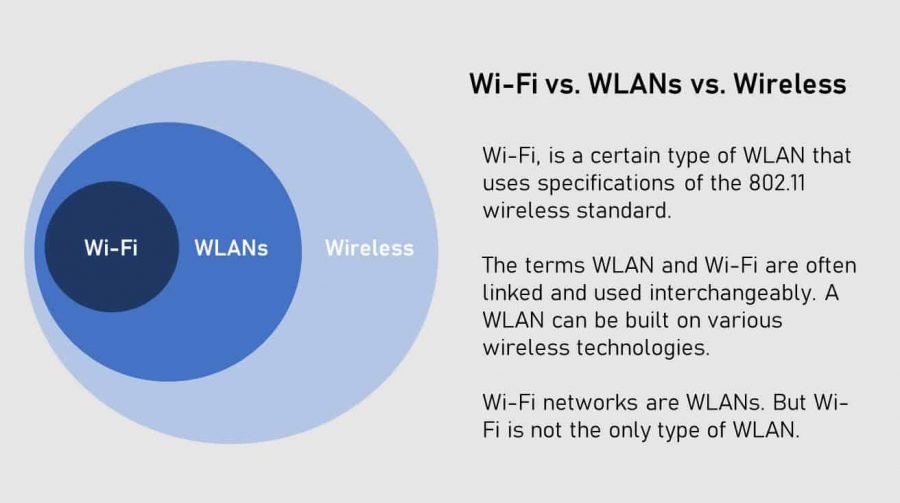
WiFi is actually a collection of different technologies working together to get bits of data wirelessly from one device to another. A wireless router is the most important device in a wireless network that connects the users with the Internet. Which of the following is the wireless network encryption method that is most secure. Wireless Local-Area Networks. The former utilises a pre-shared key PSK and is generally considered to be most suitable for home networks whereas the latter is 8021x which requires an authentication server. WiFi routers support a variety of security protocols to secure wireless networks.
 Source: businesstechweekly.com
Source: businesstechweekly.com
The 900 MHz band is the most commonly used. The frequency spectrum used in. WEP WPA and WPA2. They use IEEE 80211 standards. Which of the following is the wireless network encryption method that is most secure.
 Source: webservings.com
Source: webservings.com
The former utilises a pre-shared key PSK and is generally considered to be most suitable for home networks whereas the latter is 8021x which requires an authentication server. Understanding encryption on how it works will help you decide which protocol will protect your data. How Bandwidth Is Achieved from RF Signals. Today WPA2 is probably the most commonly used method to. A wireless router is the most important device in a wireless network that connects the users with the Internet.
 Source: pinterest.com
Source: pinterest.com
A wireless router is the most important device in a wireless network that connects the users with the Internet. WiFi is actually a collection of different technologies working together to get bits of data wirelessly from one device to another. Wireless Network Technology Difficulty. Consequently it is necessary to use robust modulation and transmission techniques to reduce the effects of narrow band interference. The rules for how data is exchanged between network nodes is known as.
 Source: etutorials.org
Source: etutorials.org
She requests that the. Therefore this type of network cannot be forged easily unlike open networks and users get privacy. It was developed to protect the wireless data between Clients and Access Points APs towards hackers. Which of the following is the wireless network encryption method that is most secure. WiFi routers support a variety of security protocols to secure wireless networks.
 Source: pinterest.com
Source: pinterest.com
There are four wireless security protocols currently available. WPA stands for WiFi Protected Access. It was developed to protect the wireless data between Clients and Access Points APs towards hackers. They use IEEE 80211 standards. Wireless Network Technology Difficulty.
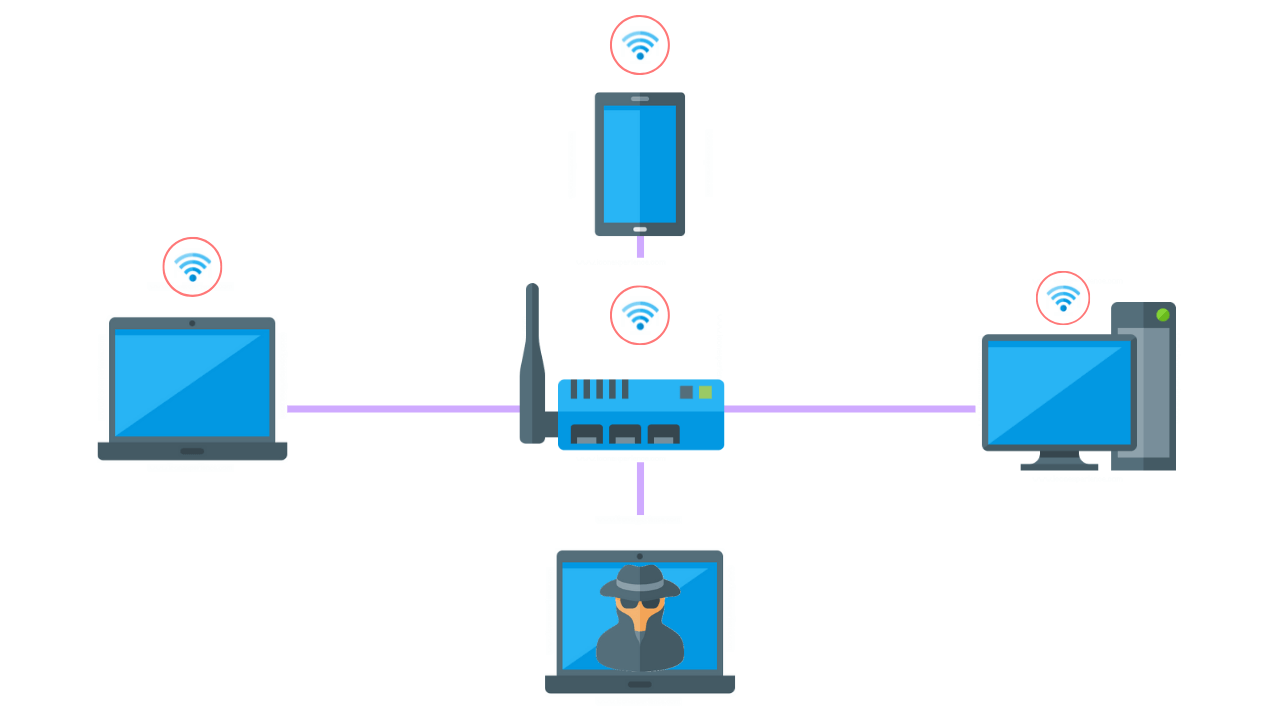 Source: purplesec.us
Source: purplesec.us
Wireless Network Technology Difficulty. The former utilises a pre-shared key PSK and is generally considered to be most suitable for home networks whereas the latter is 8021x which requires an authentication server. WiFi routers support a variety of security protocols to secure wireless networks. Wireless Local-Area Networks. Which of the following is the wireless network encryption method that is most secure.
![]() Source: ophtek.com
Source: ophtek.com
WEP WPA and WPA2. Therefore this type of network cannot be forged easily unlike open networks and users get privacy. The former utilises a pre-shared key PSK and is generally considered to be most suitable for home networks whereas the latter is 8021x which requires an authentication server. Consequently it is necessary to use robust modulation and transmission techniques to reduce the effects of narrow band interference. WiFi is actually a collection of different technologies working together to get bits of data wirelessly from one device to another.
 Source: computer-networking-success.com
Source: computer-networking-success.com
In a wireless network we have Access Points which are extensions of wireless ranges that behave as logical switches. It uses high-bandwidth connections to communicate multimedia over wireless networks. The rules for how data is exchanged between network nodes is known as. How Bandwidth Is Achieved from RF Signals. WEP WPA and WPA2.
 Source: sciencedirect.com
Source: sciencedirect.com
How Bandwidth Is Achieved from RF Signals. In a wireless network we have Access Points which are extensions of wireless ranges that behave as logical switches. She requests that the. AES in Wi-Fi leverages 8021X or PSKs to generate per station keys for all devices. WPA2 Which of the following is known as a Basic Service Set in infrastructure mode.
 Source: study.com
Source: study.com
WPA2 Which of the following is known as a Basic Service Set in infrastructure mode. AES in Wi-Fi leverages 8021X or PSKs to generate per station keys for all devices. Probably the only downside of WPA2 is how much processing power it needs to protect your network. You have quite a few options when it comes to configuring the various bits and pieces that constitute these wireless connections. WPA stands for WiFi Protected Access.
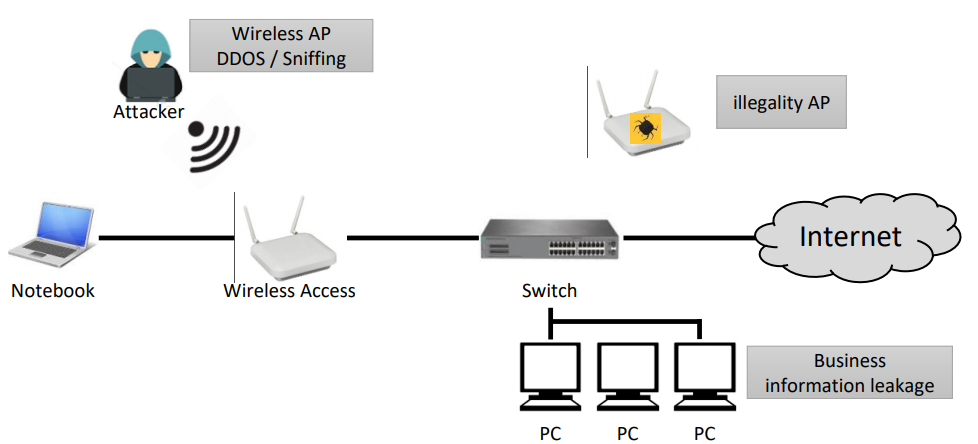 Source: safety4sea.com
Source: safety4sea.com
WPA stands for WiFi Protected Access. The 900 MHz band is the most commonly used. After the restrictions 128-bit and 256-bit WEP has developed. However these frequencies are often used by other wireless home devices such as cordless headphones or garage door openers and therefore they are subject to interference. WPS A third mode of authentication Wi-Fi Protected Setup WPS is known to be vulnerable and should be disabled on all wireless networks.
 Source: ipwithease.com
Source: ipwithease.com
In a wireless network we have Access Points which are extensions of wireless ranges that behave as logical switches. Understanding encryption on how it works will help you decide which protocol will protect your data. WiFi routers support a variety of security protocols to secure wireless networks. In a wireless network we have Access Points which are extensions of wireless ranges that behave as logical switches. WebTitan Cloud for WiFi requires no hardware purchases or software downloads as it is 100 cloud-based can be managed and monitored from any location and can help protect you against the most common wireless network attacks.
 Source: sciencedirect.com
Source: sciencedirect.com
This included the Wired Equivalent Privacy WEP algorithm which was used for security. A wireless router is the most important device in a wireless network that connects the users with the Internet. Today WPA2 is probably the most commonly used method to. This included the Wired Equivalent Privacy WEP algorithm which was used for security. How Bandwidth Is Achieved from RF Signals.
 Source: linksys.com
Source: linksys.com
How Bandwidth Is Achieved from RF Signals. Wired Equivalent Privacy WEP Wi-Fi Protected Access WPA. AES in Wi-Fi leverages 8021X or PSKs to generate per station keys for all devices. This authentication method uses different encryption algorithms to encrypt the transport. Laura a customer has instructed you to configure her home office wireless access pointShe plans to use the wireless network for finances and has requested that the network be setup with the highest encryption possible Additionally Laura knows that her neighbors have wireless networks and wants to ensure that her network is not being interfered with by the other networks.
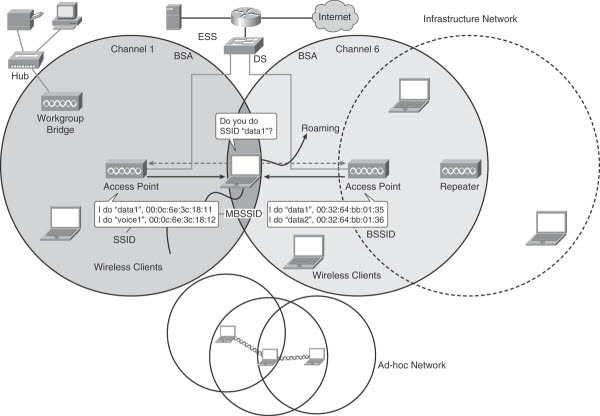 Source: blog.router-switch.com
Source: blog.router-switch.com
Laura a customer has instructed you to configure her home office wireless access pointShe plans to use the wireless network for finances and has requested that the network be setup with the highest encryption possible Additionally Laura knows that her neighbors have wireless networks and wants to ensure that her network is not being interfered with by the other networks. It was developed to protect the wireless data between Clients and Access Points APs towards hackers. The rules for how data is exchanged between network nodes is known as. After the restrictions 128-bit and 256-bit WEP has developed. They use IEEE 80211 standards.
 Source: javatpoint.com
Source: javatpoint.com
So WEP was using 64-bit encryption. Wireless Network Technology Difficulty. Wireless Security Protocols such as Wired Equivalent Privacy WEP and Wi-Fi Protected Access WPA is the authentication security protocols created by the Wireless Alliance used to ensure wireless security. WiFi routers support a variety of security protocols to secure wireless networks. The various security protocols for wireless networks use different methods to encrypt messages.
 Source: ciscopress.com
Source: ciscopress.com
At the beginning maximum 64-bit encryption was allowed in US. The various security protocols for wireless networks use different methods to encrypt messages. In a wireless network we have Access Points which are extensions of wireless ranges that behave as logical switches. Today WPA2 is probably the most commonly used method to. Understanding encryption on how it works will help you decide which protocol will protect your data.
 Source: what-when-how.com
Source: what-when-how.com
Today WPA2 is probably the most commonly used method to. Wireless Network Technology Difficulty. Although wireless networks offer great flexibility they have their security. WEP was widely used but it has too vulnerable to the password hacks. This authentication method uses different encryption algorithms to encrypt the transport.
This site is an open community for users to do sharing their favorite wallpapers on the internet, all images or pictures in this website are for personal wallpaper use only, it is stricly prohibited to use this wallpaper for commercial purposes, if you are the author and find this image is shared without your permission, please kindly raise a DMCA report to Us.
If you find this site serviceableness, please support us by sharing this posts to your own social media accounts like Facebook, Instagram and so on or you can also bookmark this blog page with the title which of the following is the most widely used wireless network encryption for home wireless networks by using Ctrl + D for devices a laptop with a Windows operating system or Command + D for laptops with an Apple operating system. If you use a smartphone, you can also use the drawer menu of the browser you are using. Whether it’s a Windows, Mac, iOS or Android operating system, you will still be able to bookmark this website.
Category
Related By Category
- 31++ Best keto bars info
- 24+ Moro de gandules recipe info
- 23++ Bamboo plant care indoor information
- 27+ Pasta fagioli recipe info
- 27+ Can guinea pigs eat apples ideas in 2021
- 50+ Diy brazilian wax ideas
- 45+ Perennial garden information
- 21+ Birmingham zoo christmas lights ideas in 2021
- 41+ Crater road veterinary hospital info
- 24+ Disney world travel agent ideas